Feistel Ciphers: Security Proofs and Cryptanalysis

Feistel ciphers are a class of block ciphers that are widely used in cryptography. They were first introduced by Horst Feistel in 1973, and have since been used in a variety of applications, including the Data Encryption Standard (DES) and the Advanced Encryption Standard (AES).
5 out of 5
| Language | : | English |
| File size | : | 11967 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 519 pages |
| Paperback | : | 132 pages |
| Item Weight | : | 7.1 ounces |
| Dimensions | : | 5.63 x 0.47 x 8.9 inches |
Feistel Cipher Structure
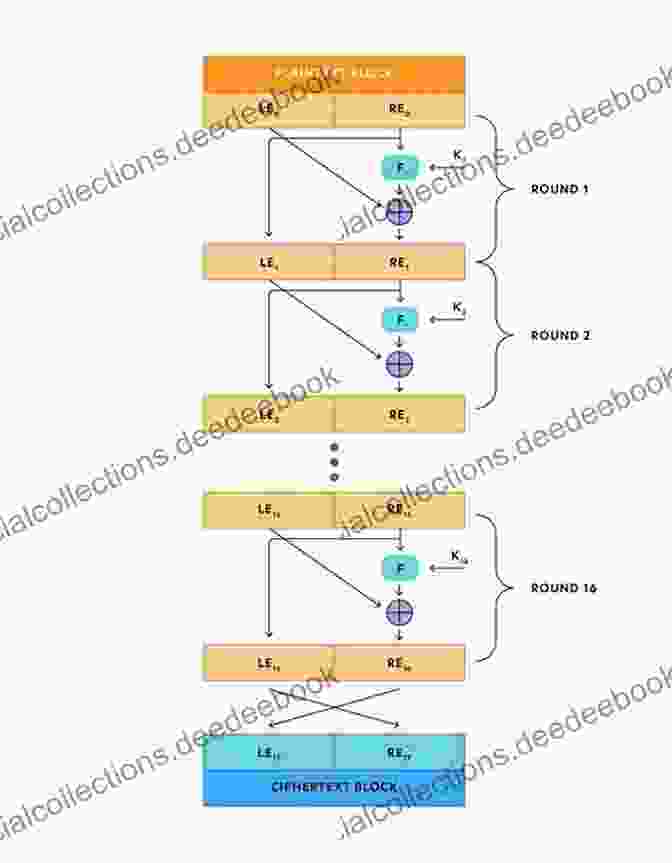
A Feistel cipher consists of a number of rounds, each of which consists of two sub-rounds. In each sub-round, the input block is divided into two halves, and each half is processed by a separate function. The outputs of the two sub-rounds are then combined to form the input to the next round.
The key schedule for a Feistel cipher is typically generated from the secret key using a key expansion algorithm. The key expansion algorithm is designed to produce a different key for each round of the cipher.
Security Proofs
There are a number of security proofs that have been developed for Feistel ciphers. These proofs show that Feistel ciphers are resistant to a variety of cryptanalytic attacks, including differential cryptanalysis, linear cryptanalysis, and impossible differential cryptanalysis.
Differential cryptanalysis
Differential cryptanalysis is a cryptanalytic technique that exploits the differences between the outputs of a cipher for two different inputs. In order to be resistant to differential cryptanalysis, a cipher must have a high diffusion rate. This means that the output of the cipher should be highly sensitive to changes in the input.
Feistel ciphers have a high diffusion rate because the input block is divided into two halves in each round, and each half is processed by a separate function. This means that any change in the input block will propagate through the cipher in a complex way, making it difficult to predict the output.
Linear cryptanalysis
Linear cryptanalysis is a cryptanalytic technique that exploits the linear relationships between the input and output of a cipher. In order to be resistant to linear cryptanalysis, a cipher must have a low linearity. This means that the output of the cipher should not be linearly related to the input.
Feistel ciphers have a low linearity because the two sub-rounds in each round are independent of each other. This means that the output of the cipher is not simply a linear combination of the inputs to the two sub-rounds.
Impossible differential cryptanalysis
Impossible differential cryptanalysis is a cryptanalytic technique that exploits the fact that certain combinations of inputs and outputs are impossible for a given cipher. In order to be resistant to impossible differential cryptanalysis, a cipher must have a high probability of producing all possible outputs.
Feistel ciphers have a high probability of producing all possible outputs because the two sub-rounds in each round are independent of each other. This means that the output of the cipher is not simply a deterministic function of the input.
Cryptanalysis
Despite the security proofs that have been developed for Feistel ciphers, there have been a number of successful cryptanalytic attacks on Feistel ciphers. These attacks have shown that Feistel ciphers are not perfect, and that they can be broken with sufficient effort.
Weak key attacks
Weak key attacks are cryptanalytic attacks that exploit weaknesses in the key schedule of a cipher. These attacks can be used to recover the secret key from a known plaintext-ciphertext pair.
Feistel ciphers are particularly vulnerable to weak key attacks because the key schedule is typically generated from the secret key using a simple algorithm. This makes it possible for an attacker to find weak keys by brute force.
Related-key attacks
Related-key attacks are cryptanalytic attacks that exploit the relationships between different keys. These attacks can be used to recover the secret key from a known plaintext-ciphertext pair, even if the keys are not related in a known way.
Feistel ciphers are particularly vulnerable to related-key attacks because the key schedule is typically generated from the secret key using a simple algorithm. This makes it possible for an attacker to find related keys by brute force.
Side-channel attacks
Side-channel attacks are cryptanalytic attacks that exploit information that is leaked from the implementation of a cipher. These attacks can be used to recover the secret key from a known plaintext-ciphertext pair, even if the cipher is implemented correctly.
Feistel ciphers are particularly vulnerable to side-channel attacks because they are often implemented in software. This makes it possible for an attacker to use timing attacks or power analysis to extract information about the secret key.
Feistel ciphers are a widely used class of block ciphers that are resistant to a variety of cryptanalytic attacks. However, there have been a number of successful cryptanalytic attacks on Feistel ciphers, and it is important to be aware of these attacks when using Feistel ciphers in cryptographic applications.
5 out of 5
| Language | : | English |
| File size | : | 11967 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 519 pages |
| Paperback | : | 132 pages |
| Item Weight | : | 7.1 ounces |
| Dimensions | : | 5.63 x 0.47 x 8.9 inches |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Bibliography
Bibliography Foreword
Foreword Preface
Preface Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Tome
Tome Narrative
Narrative Biography
Biography Memoir
Memoir Thesaurus
Thesaurus Character
Character Librarian
Librarian Catalog
Catalog Card Catalog
Card Catalog Borrowing
Borrowing Stacks
Stacks Archives
Archives Periodicals
Periodicals Research
Research Lending
Lending Reserve
Reserve Academic
Academic Journals
Journals Reading Room
Reading Room Special Collections
Special Collections Thesis
Thesis Dissertation
Dissertation Storytelling
Storytelling Awards
Awards Reading List
Reading List Book Club
Book Club Mckenzie Wark
Mckenzie Wark Luis Portas
Luis Portas Alexandre Debs
Alexandre Debs Erin Mc Luckie Moya
Erin Mc Luckie Moya Joseph Postell
Joseph Postell Lexi Post
Lexi Post David Lafferty
David Lafferty Roksy Store Publishing
Roksy Store Publishing Leendert M Huisman
Leendert M Huisman Mark Ager
Mark Ager Steve Clapp
Steve Clapp Samuel Stein
Samuel Stein Helen Rolfe
Helen Rolfe Gary Berntsen
Gary Berntsen J D Salinger
J D Salinger Amanda Ross
Amanda Ross L L Bartlett
L L Bartlett Lida Maxwell
Lida Maxwell Daryl Farmer
Daryl Farmer Michael Morpurgo
Michael Morpurgo
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Jermaine PowellPersonal Transformations in Small Groups: A Comprehensive Guide to Empowering...
Jermaine PowellPersonal Transformations in Small Groups: A Comprehensive Guide to Empowering... Jarrett BlairFollow ·9.4k
Jarrett BlairFollow ·9.4k Ken SimmonsFollow ·11.8k
Ken SimmonsFollow ·11.8k Walter SimmonsFollow ·12.8k
Walter SimmonsFollow ·12.8k Arthur MasonFollow ·14.9k
Arthur MasonFollow ·14.9k Roger TurnerFollow ·14.4k
Roger TurnerFollow ·14.4k Edgar CoxFollow ·18.7k
Edgar CoxFollow ·18.7k Edwin BlairFollow ·2k
Edwin BlairFollow ·2k Cason CoxFollow ·12.8k
Cason CoxFollow ·12.8k

 Andy Hayes
Andy HayesEmbracing Now: Embark on a Mindfulness Journey for a...
In a world...

 Heath Powell
Heath Powell100 Hymns for Violin and Guitar: A Comprehensive Guide to...
The violin and...

 Floyd Richardson
Floyd RichardsonBark In The Park: Poems For Dog Lovers
Dogs are our best...

 Douglas Adams
Douglas AdamsThe Barter Crusade: A Journey into the Realm of Exchange...
In a world driven by monetary transactions,...

 Nathaniel Hawthorne
Nathaniel HawthorneInsight Guides Explore Nice & the French Riviera...
Prepare to embark on an unforgettable journey...

 Carlos Fuentes
Carlos FuentesThe Ultimate Practical Guide to Percussion: Exploring the...
Embark on a journey into the enchanting...
5 out of 5
| Language | : | English |
| File size | : | 11967 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 519 pages |
| Paperback | : | 132 pages |
| Item Weight | : | 7.1 ounces |
| Dimensions | : | 5.63 x 0.47 x 8.9 inches |